For a business, computers, information, internet are extremely important factors related to the survival and development of businesses no matter how big or small. The network supports applications and provides services and resources for businesses to operate, from which they can provide services to users. Today's business needs are increasing, along with the complexity of network infrastructure. Given a problem is how to design a good infrastructure that works 100% of the time with heavy traffic and avoids unexpected security incidents.
There are 4 goals set in the construction of network infrastructure that are:
- Must be scalable: as the business grows, the number of users will also increase, so the infrastructure must be able to grow to accommodate the number of new users without affecting the services of the users. old use.
- Must be able to operate 100% of the time: the network system must operate stably, reliably, and can run 24/7.
- Must ensure security: security devices must be designed during system design, not added after the system is complete. This will protect your network resources.
- Must be able to manage: the system must be easily managed and supported to handle and fix problems in the most effective way.
1. Principles of network construction
1.1. Hierarchical network model
The hierarchical network model and modular design are developed by most large companies and corporations because:
Simple and easy when expanding more buildings, WAN connections, branches, affiliated offices, new modules such as E-banking, VPN...
The upgrade or expansion only changes the locality or area connected to it, and does not affect all other functional modules.
The network system can be doubled or tripled without affecting the original structure and design.
Simplicity in isolating and troubleshooting. This is extremely important for large networks with hundreds or thousands of routers.
The 3-layer hierarchical design model will be applied in both WAN and Campus network design. The general structure of a hierarchical model includes 3 layers Core, Distribution and Access.
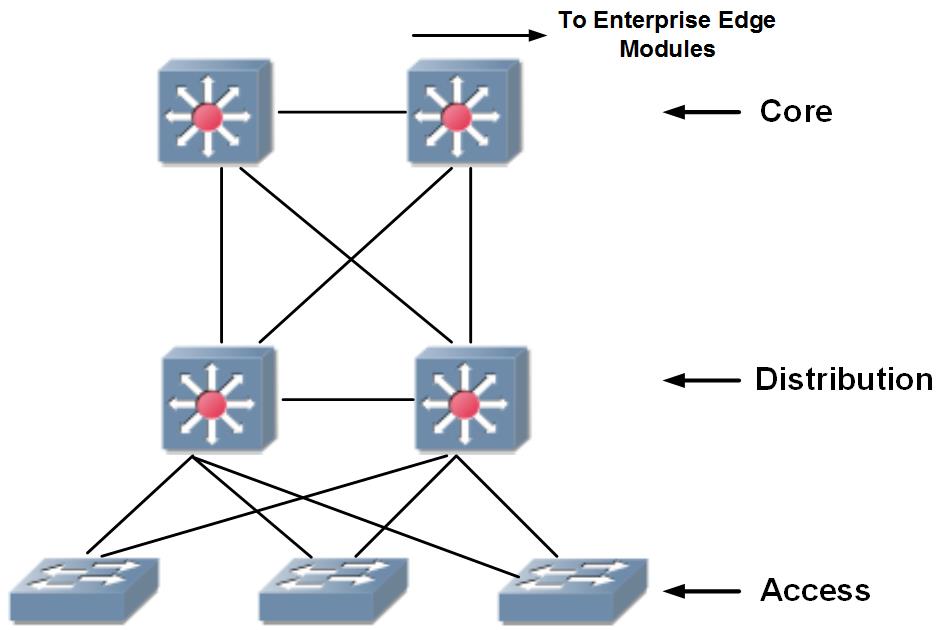
1.2. Redundant network structure
Availability of service: Customers always need to access the service system anywhere, anytime, through many different means such as Internet, SMS, Telephone .. Ensuring availability in supply Providing service to customers has become a mandatory requirement for information technology systems. Losses due to service interruptions are not limited to the number of customers and transaction value at the time of the interruption.
Data security: The integrity of the data needs to be protected and accessible. Factors to consider:
Ensure backup mechanism
Redundancy for transmission lines (internet, WAN, etc.)
Power backup: Important equipment ensures that there are always 2 sources of use, 1 main source of operation and 1 backup source.
Redundancy helps to avoid a situation where the entire system is lost due to a single device failure.
1.3 Virtualization network structure
When building a Data Center, the next step of centralization (Data Center Consolidation) is the implementation of Data Center Virtualization (Data Center Virtualization). This phase of virtualization allows Data Center administrators to create virtual, abstraction layers between applications, host systems, and network infrastructure.
Data Center Virtualization is the creation of a logical entity from physical entities, or the creation of multiple logical entities from a single physical entity. These entities can be computing devices, storage systems, networks, or applications. Thus, it is possible to virtualize most of the components that make up the Data Center, from network services, storage systems, computing systems, and connectivity components, as shown in Fig. down here.
Implementing Data Center virtualization enables increased efficiency of data center resources, faster service delivery, and reduced impact on the availability of applications at the data center. Data center when performing maintenance. Furthermore, one of the key benefits of virtualization is being able to create independent, separate, secure IT infrastructures based on a single physical infrastructure. These virtualized stand-alone IT infrastructures support different workgroups, supporting different member infrastructures on a single physical platform.
1.4. Network security
Ensuring information security is also a very important requirement for the network system. This is an element that needs to be carefully considered in the design.
According to a survey by the Computer Security Institute (CSI), up to 70% of organizations admit their networks have been hacked, and up to 60% of intrusions are made from within the organization. there. It demonstrates that network security is not only enforced against outside access, it must also be implemented itself from within the organization's network.
In addition, in addition to the problem of illegal access, viruses are also causing discomfort for users. Previously when computers were independent of each other, the virus that affected the computer was also located on the infected computer. Today, when computers are networked together, one computer is infected, the risk of infection throughout the network is possible.

1.5. Modular structure
The network system is divided into functional blocks and clear areas
- System of regional centers and systems of provincial and district branches
- Separate function blocks (Core , Management, Edge ..)
- The modularization of the system ensures
- Easy for administration, operation, upgrade, change..
- Changes and upgrades inside each block do not affect other blocks. With each block only interested in the remaining areas in terms of physical interface communication and service delivery.
1.6. Optimizing the network system
With a large network, including many devices, optimizing the system will bring many benefits:
- Reduce the risk of system operation failure
- Increase system operating capacity
- Reduce the need for investment, equipment upgrade
- Measures to optimize the network system of YYY Bank can be implemented:
- IP address planning and optimization: This is an extremely important step, a well-planned IP address allocation will be the premise to build a stable, high-capacity and easy-to-expand network system, upgrade
- Routing optimization: Using the right routing protocol, planning the network according to the appropriate areas. Using techniques such as: Route Sumarization, Routing Filtering, Load-balancing ... will help increase system capacity and make the most of the performance of each device and transmission line.
- Deploying QoS: Deploying QoS will reduce WAN, Internet bandwidth and improve the performance of applications, especially applications such as Voice, Video.
1.7. Firm strategy
System of one, or many firms (Single Vendor vs Multi-Vendor)
2. Network design criteria
2.1. Functionality
Functionality is the most important criterion. A real IT system only makes sense when it properly and fully meets the requirements of the business and the objectives and functions have been set out.
2.2. Performance (Processing capacity)
As one of the most important components on a network, Performance is defined by bandwidth and the rate at which data can be transmitted per unit of time in Seconds (pps). Due to the complexity when calculating the full Processing Capacity, people will focus on 3 influencing factors that are most related to the Processing Capacity to be able to recognize a network, that is:
- Responsiveness (response time)
- Throughput (Bandwidth)
- Utilization (Optimization)
The most important thing after investing in upgrading is the processing capacity of the network. The response time of the applications on the network must be within the time allowed at the times when the network is operating at its peak. To do this, Throughput on the network must always ensure stability and optimize bandwidth (Utilization). The optimal here is the performance of the device so that it is able to meet the requirements that are brought in rapidly.
2.3. Scalability
The network system will inevitably expand, so any additional investment or upgrade must take into account scalability. The scalability problem can be divided into two types as hard expansion and soft expansion.
Hard expansion here can be understood as the possibility of upgrading with existing devices. Devices must have extensions such as Modules, Slots, Cards.. To do that, the administrator as well as the designer must be able to decentralize the system, partition and clearly define the tasks of each other area. each other to get the most accurate view of the network, in order to facilitate adjustment and upgrade.
Soft scaling is also an important point. The network administrator will have to be able to predict the extent of the network so that he can determine the type of routing protocol to be used on the network (to avoid very complicated routing protocol changes) and have an IP address plan (IP Plan) that best suits the network.
2.4. Availability (Stability)
Stability (Availability) is calculated as follows:
Availability(Intrinsic) A i = MTBF / (MTBF + MTTR)
An important point when designing a network is stability. Stability is defined as the system downtime (MTTR: mean time to repair) must be minimized and the time to run without failure (MTBF: meatime between failure) must be maximized. Therefore, there are some points we need to pay attention to when talking about stability as follows:
- Equipment redundancy
- Transmission redundancy
- Routing protocol redundancy
2.5. Manageability
The network system can only be operated effectively if it is well managed. The management ability should ensure the following contents:
Fault Management: The ability to detect and notify when an error occurs on the network
Configuration Management: the ability to manage the configuration of the device. This management capability includes configuration file management, device statistics and software management, as well as logging of configuration changes.
System Auditing (Accounting Management): the ability to manage and control the overall system from an intermediary perspective.
Performance Management: The ability to collect information from devices and transmissions, display the usage status of devices and transmissions to make appropriate decisions.
Security Management: The ability to manage, set, and monitor security policies across the network.
2.6. Cost Effectiveness
Cost Effectiveness is not simply about cutting costs as much as possible. Cost savings in design need to be understood more broadly than the ability to utilize the investment optimally to bring about efficiency. Shown in the following:
- Reasonable use of equipment
- Develop a suitable roadmap, avoid wasting equipment depreciation
INTELLIGENT TECHNOLOGY SERVICES JOINT STOCK COMPANY specializes in consulting, designing, providing network and telecommunications infrastructure solutions for large and small businesses. Depending on the actual needs of each customer, we can provide application systems based on different technologies that bring the highest efficiency at the most suitable price. Contact us immediately to get the best solution and quote.
-----------------------------------
Contact Info:
Website: https://ites.vn/
Hotline: 028 3883 2324
Email: info@ites.vn
